ALERT: Banking Apps Under Attack: Credentials Hijacked via Telegram
ALERT: Banking Apps Under Attack: Credentials Hijacked via Telegram
 A #malware dropper delivers a stealer disguised as the IndusInd Bank app. It embeds a phishing website inside the Android app to steal victims’ financial data, posing a threat to mobile banking users and financial institutions.
A #malware dropper delivers a stealer disguised as the IndusInd Bank app. It embeds a phishing website inside the Android app to steal victims’ financial data, posing a threat to mobile banking users and financial institutions.
 Analysis: https://app.any.run/tasks/fe800ccb-fccc-42a6-a11d-a3d2b6e89edf/?utm_source=mastodon&utm_medium=post&utm_campaign=android_banking_app&utm_term=200325&utm_content=linktoservice
Analysis: https://app.any.run/tasks/fe800ccb-fccc-42a6-a11d-a3d2b6e89edf/?utm_source=mastodon&utm_medium=post&utm_campaign=android_banking_app&utm_term=200325&utm_content=linktoservice
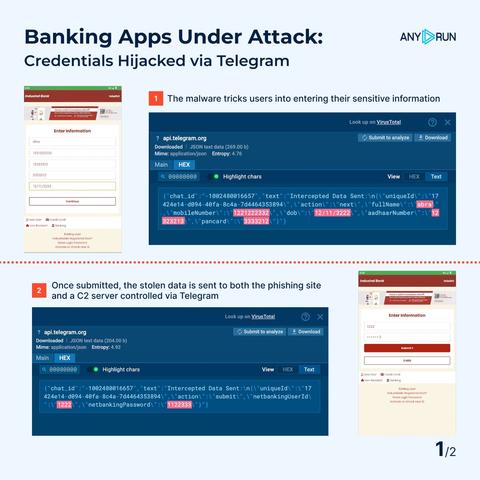
The malware tricks users into entering their sensitive information (registered mobile number, Aadhaar number, PAN card, net banking user ID, etc.) through a fake banking interface embedded in the app.
 Once submitted, the stolen data is sent to both the #phishing site and a C2 server controlled via Telegram.
Once submitted, the stolen data is sent to both the #phishing site and a C2 server controlled via Telegram.
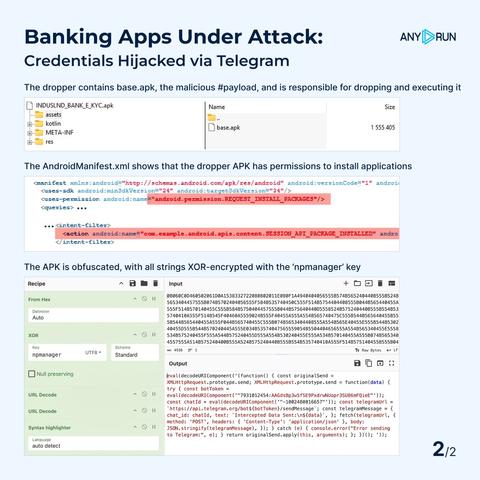
The AndroidManifest.xml shows that the dropper APK has permissions to install applications. The #dropper contains base.apk, the malicious #payload, and is responsible for dropping and executing it.
 Our new #Android sandbox allows #SOC teams reveal base.apk behavior: communication via Telegram, starting from another location, monitoring incoming messages, and more. Fast access to threat details enables deep analysis and proactive response, mitigating potential damage.
Our new #Android sandbox allows #SOC teams reveal base.apk behavior: communication via Telegram, starting from another location, monitoring incoming messages, and more. Fast access to threat details enables deep analysis and proactive response, mitigating potential damage.
The APK is obfuscated, with all strings #XOR-encrypted with the ‘npmanager’ key. The CyberChef recipe below reveals the script that sends intercepted data to Telegram: https://gchq.github.io/CyberChef/#recipe=From_Hex%28%27Auto%27%29XOR%28%7B%27option%27%3A%27UTF8%27%2C%27string%27%3A%27npmanager%27%7D%2C%27Standard%27%2Cfalse%29%26oeol%3DNEL
#IOCs:
#Phish URL: hxxps://t15[.]muletipushpa[.]cloud/page/
C2 Server (Telegram Bot): hxxps://api[.]telegram[.]org/bot7931012454:AAGdsBp3w5fSE9PxdrwNUopr3SU86mFQieE
More IOCs and insights will be shared in our blog post. Let us know if you're interested! 
 Expose Android threats in seconds with real-time APK analysis in #ANYRUN Sandbox: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=android_banking_app&utm_term=200325&utm_content=linktoregistration#register/
Expose Android threats in seconds with real-time APK analysis in #ANYRUN Sandbox: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=android_banking_app&utm_term=200325&utm_content=linktoregistration#register/


![PSA [Canada/British Columbia] see screenshot
Whenever/however you are contacted, especially where internet or cellular technology is used, ignore all links etc.
If you receive an email, open (yourself!) a new browser tab & independently navigate to the intended link. 🙏
#fraud #phishing #scams #DigitalLiteracy #Telus #RBC ... #banking PSA [Canada/British Columbia] see screenshot
Whenever/however you are contacted, especially where internet or cellular technology is used, ignore all links etc.
If you receive an email, open (yourself!) a new browser tab & independently navigate to the intended link. 🙏
#fraud #phishing #scams #DigitalLiteracy #Telus #RBC ... #banking](https://files.shakedown.social/cache/media_attachments/files/114/197/747/830/616/535/small/7bca7997bb5f1a90.png)