Dealing with something ridiculous at the moment that is a great example of just how 'easy' it really is to close down exposed data:
Found a server recently with no access controls at all that was hit by ransomware in May 2024 and most of the data is encrypted. (It got hit by an automated script, it wasn't targeted by a ransom group)
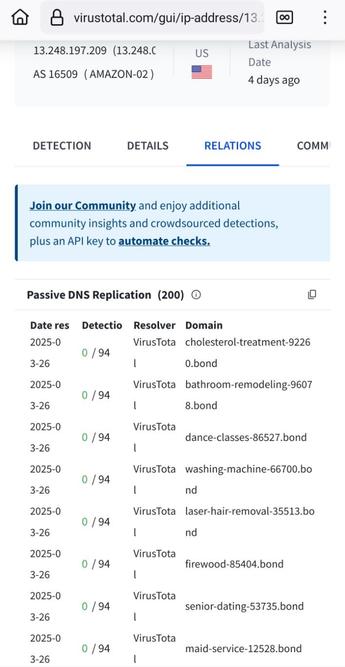
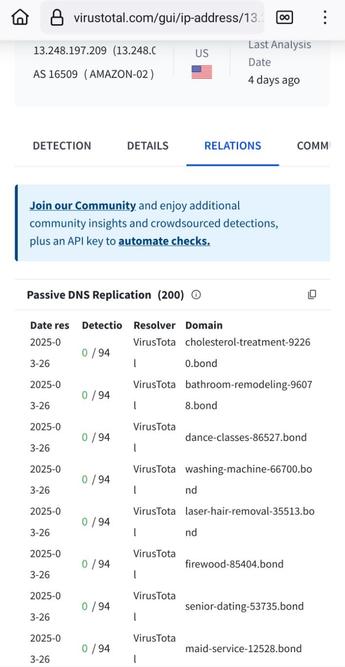
Found a non encrypted directory:
The company is STILL uploading, monthly, hundreds of millions of records of logs with their clients data.
Tried to reach out to the company, nothing. Company is from AUS so I tried ASD, nothing.
I sent an email to AUSCERT, they validated with me the issue and forwarded the information and my contact to ASD, they also tried to reach out to the company themselves.
Not a word from anyone and the server is still exposed a month after my initial alerts.
Logs are still being uploaded to the server so it's obvious no one did anything.
So what am I supposed to do here?