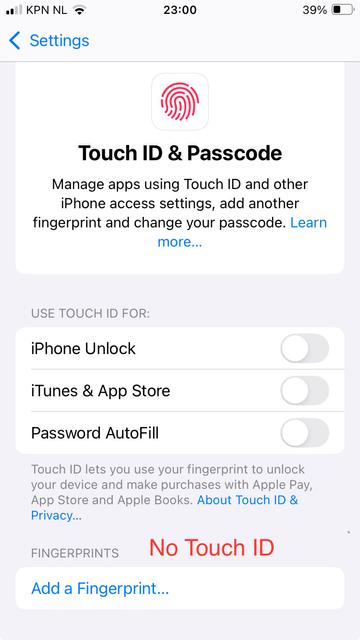
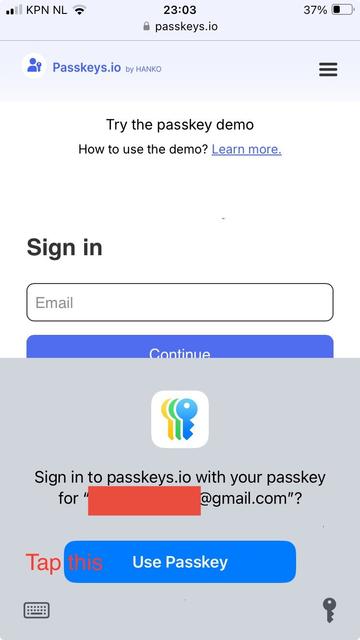
@zak @zenbrowser : a still unfixed vulnerability: if NOT using Touch ID, on some websites you may be able to sign in using a passkey WITHOUT authenticating locally - using biometrics or your passcode (screen unlock code).

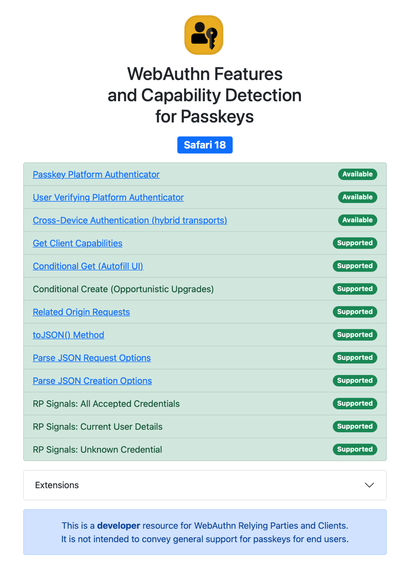
 This vulnerability also exists WITH Touch ID set up, provided that "Password Autofill" is disabled.
This vulnerability also exists WITH Touch ID set up, provided that "Password Autofill" is disabled.
BTW this vulnerability also permits access to:
• https://icloud.com
• https://account.apple.com
(When asked to provide your fingerprint, tap the X at the top right and tap in the "Email" field one more time).
This is a HUGE risk for people who do not want to use biometrics: if a thief grabs their iPhone when unlocked, or watches them enter their passcode and later steals their iPhone, the thief can use ALL of the owner's passwords and some of their passkeys stored in the "Passwords" app (formerly known as iCloud Keychain).
 This increases the risks of theft as shown by WSJ's Joanna Stern in https://youtube.com/watch?v=QUYODQB_2wQ.
This increases the risks of theft as shown by WSJ's Joanna Stern in https://youtube.com/watch?v=QUYODQB_2wQ.
 In addition, a (grand) child or anyone else who (shortly) borrows your iPhone/iPad may have access to more of your cloud-accounts than you're aware of.
In addition, a (grand) child or anyone else who (shortly) borrows your iPhone/iPad may have access to more of your cloud-accounts than you're aware of.
 Workaround if you don't want to use biometrics to unlock your iPhone/iPad (this does not fix any problem if a thief learns (or successfully guesses) your passcode (screen unlock PIN or password):
Workaround if you don't want to use biometrics to unlock your iPhone/iPad (this does not fix any problem if a thief learns (or successfully guesses) your passcode (screen unlock PIN or password):
• Set up a Touch ID anyway, for example for your left pinky finger (if you're righthanded)
• Disable "iPhone Unlock" in "Touch ID and Passcode" (visible in the first screenshot).
• Use a safer password manager (such as KeePassium) than the Apple "Passwords" app (iCloud KeyChain).
 In any case:
In any case:
• Make sure that "Password Autofill" (in settings -> "Touch ID and Passcode") is set to ENABLED;
• When you enter your passcode in a public place (such as a bar, bus or train), make very sure that nobody gets to see you enter it.