Recent searches
Search options
#dfir
Investigation Scenario
You have detected unauthorized modification to /etc/libaudit.conf on a Linux server.
What do you look for to investigate whether an incident occurred and its impact? What could an attacker have done here?
How do you identify a cybersecurity incident?
@hacks4pancakes sees a lot of copy/paste incident responses on the Internet - you really need to understand what matters to your business. Sarah Sabotka argues that this is where CTI comes in to support incident response to see what we can enrich. Per@DavidJBianco, the Identify stage is all about going from raw data up and to engaging your incident response plan.
Catch the full discussion from this past week's episode of the Breaking Badness Cybersecurity Podcast here: https://podcasts.apple.com/us/podcast/dfirside-chat-lessons-from-the-frontlines-of/id1456143419?i=1000703745188
New Open-Source Tool Spotlight
Google's GRR (GRR Rapid Response) is an open-source framework for remote live forensics and incident response. It allows security teams to investigate systems at scale without interrupting operations. Used for data collection, analysis, and hunting. #CyberSecurity #DFIR
Project link on #GitHub
https://github.com/google/grr
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking
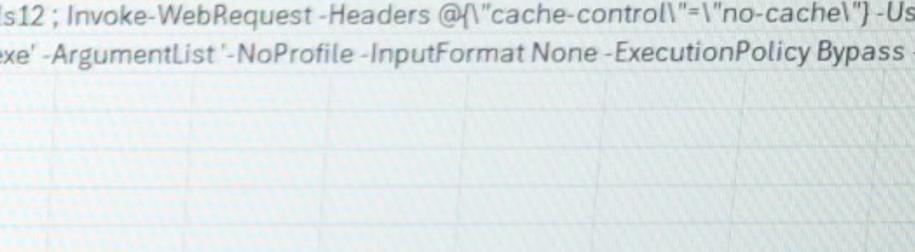
This NLRB whistleblower complaint is a horror story for any CERT team. As a CTI/SOC analyst, if I see spawned powershell invoking web requests to some random-ass AI API reverse-engineering tool/headless browser repository, large outbound byte transfers measured in GBs, or conditional access policies/MFA being tampered with, you’re getting isolated and we’re standing up an incident response bridge. Also, someone on your team has an info stealer on their device if they’re seeing attempted logins from a foreign country within fifteen minutes of account creation.
This is an insider threat case of the worst kind: one your security team gets to watch but can’t do a damn thing to stop.
Is the tool vendor provided training subject to tariffs too?
In the course of its investigations, @volexity frequently encounters malware samples written in Golang. This reflects the increase in popularity of the Golang generally, and presents challenges to reverse engineering tools.
Today, @volexity is releasing GoResolver, open-source tooling to help reverse engineers understand obfuscated samples. @r00tbsd & Killian Raimbaud presented details at INCYBER Forum earlier today.
GoResolver uses control-flow graph similarity to identify library code in obfuscated code, leaving analysts with only malware functions to analyze. This saves time & speeds up investigations!
Check out the blog post on how GoResolver works and where to download it: https://www.volexity.com/blog/2025/04/01/goresolver-using-control-flow-graph-similarity-to-deobfuscate-golang-binaries-automatically/
#dfir #reversing #malwareanalysis
Security tips of the day:
logs only need to be stored 3 days, that's enough to cover a weekend
if you don't store backups, you also don't need to restore them
having less internal defenses decreases how long an attack takes, so you're back online faster
domain-join everything (especially firewalls and backups) to decrease dwell time of attackers
antivirus logs should never be monitored to reduce workload of analysts
never publish vulnerabilities: if no one knows about them, no one can exploit them ever.
For more security tips, follow my Tesla account.
2025-03-28 RDP #Honeypot IOCs - 181569 scans
Thread with top 3 features in each category and links to the full dataset
#DFIR #InfoSec
Top IPs:
138.199.24.6 - 91545
156.146.57.110 - 42849
156.146.57.52 - 10716
Top ASNs:
AS60068 - 93561
AS212238 - 64269
AS135161 - 10653
Top Accounts:
hello - 181455
Test - 33
eltons - 15
Top ISPs:
DataCamp Limited - 93561
Datacamp Limited - 64269
GMO-Z.COM PTE. LTD. - 10653
Top Clients:
Unknown - 181569
Top Software:
Unknown - 181569
Top Keyboards:
Unknown - 181569
Top IP Classification:
hosting & proxy - 160374
hosting - 10710
Unknown - 10440
Pastebin links with full 24-hr RDP Honeypot IOC Lists:
https://pastebin.com/BiF6s8Jh
Mini Blue Team Diaries story:
There was a break-in over the weekend at one of our US offices. We occupied one floor of a shared office building, and two crooks managed to get in by going to an open floor above ours and breaking a lock on the fire escape.
Rather brilliantly, a building security guard was doing rounds and actually caught the pair stuffing iPads from conference rooms into a rucksack. However, when challenged they claimed to be employees and were left alone.
Anyway they ended up with about a half dozen iPads from Zoom rooms. Annoying but not the end of the world.
Those iPads were clearly sold on, as they were connected to an MDM server and started to pop up in locations all over the city over the course of the next week.
One of them was especially interesting. Because it was connected to our MDM Apple ID, it was syncing files to iCloud. This included photos. We noticed a lot of selfies of one particular dude show up. The dude looked a lot like one of the guys who we’d seen in our office on our security cameras. Yup.
We of course passed on all the information, including the location of the selfie generating iPad, to law enforcement.
I wish there was a more interesting ending - but they never followed up on the lead, of course. So the iPads lived on, slowly filling up with various photos and memories from the crook and the people they’d been sold on to.
Read more, slightly less mini stories, at infosecdiaries.com
Fun Linux DFIR question for you! You're looking at your SSH logs and you find a root login using pubkey auth:
2025-03-20T07:44:00-0400 labpc sshd[15420]: Accepted publickey for root from 10.1.1.5 port 46698 ssh2: ED25519 SHA256:6ynkM0+FOrHtoQlkPOOQ415tvRGdBaBEMs2KWtGB1Bo
There are multiple keys in /root/.ssh/authorized keys. How can you tell which one was used for this login?
Investigation Scenario
Proxy logs show a Linux database server making HTTP requests with an empty User Agent string.
You don't have PCAP or other network logs.
What do you look for to investigate whether an incident occurred?
If you can't explain how it works, what will you do when it doesn't work?
There is a new #Fediverse bot that facilitates web forensic analysis of websites.
You can submit a domain for crawling by messaging @lookyloo, and it will respond with the analysis results.
#cybersecurity #threatintel #dfir
services is provided by @circl
Thanks to @rafi0t for the new bot.
Coty Tuggle put together this cool lightweight incident tracking framework (adapted from earlier work by CrowdStrike). If you're dealing with Windows event logs in your investigation, this looks like a great resource for individual analysts to organize their investigations and produce incident timelines in a reproducible manner. Coty's example does it with Splunk, but it should be easy to adapt his framework to your preferred log analysis platform.
https://medium.com/@ctugglev/you-can-run-but-my-tracker-is-faster-38f9bacaf324
TR-93 - Financial transaction fraud after system compromise.
This document outlines a malspam attack targeting businesses through fraudulent emails that exploit Remote Monitoring & Management (RMM) tools. The attackers deceive recipients into clicking a malicious link disguised as an invoice, which installs an RMM tool on their system. Since these tools are legitimate applications, they evade antivirus detection.
Where in the world is Daniel Schwalbe? Give us your best guesses in the comments!
Daniel walks through why you should sign up for DomainTools upcoming panel discussion on the Foundations of DFIR.
You can save your spot here: https://www.domaintools.com/webinar-getting-back-to-the-foundations-of-dfir/?utm_source=LinkedIn&utm_medium=Social&utm_campaign=DFIR-To-You
Super happy to see the open source sysdiagnose joining the hackathon.lu held in Luxembourg on April 8th and 9th, 2025.
sysdiagnose is an open-source framework developed to facilitate the analysis of the Apple sysdiagnose files and especially the one generated on mobile devices (iOS / iPadOS). In the light of targeted attacks against journalists, activist, representatives from the civil society and politicians, it empowered incident response team to review device behaviour and ensure their integrity. This tool is initially the result of a joint effort between EC DIGIT CSOC (European Commission DG DIGIT) and CERT-EU (https://cert.europa.eu/).
https://hackathon.lu/projects/#sysdiagnose-analysis-framework
Don't hesitate to register and add your project!
#opensource #dfir #forensic #hackathon #luxembourg
Thanks to @ddu and the team to join us.